Comptia Network+ Â⮠Lab Series Network Concepts Lab 7 Remote Access - Rdp 23 Review Questions
What Is Remote Desktop?
 Calculating used to be highly dependent on location. The original mainframes had no network connexion at all – any work done on the machine had to be done in the same room. Eventually, networking and personal computers extended the accomplish of calculating activity. For quite a long time, though, most business-related computing tasks were performed within the office walls. Even as laptops became pop and people started working from a dwelling estimator, the piece of work was typically limited. Certain systems could not be accessed from habitation or certain tasks could not be completed because of low bandwidth. As engineering science has improved, many options are now available for enabling remote work. One of the most popular is remote desktop.
Calculating used to be highly dependent on location. The original mainframes had no network connexion at all – any work done on the machine had to be done in the same room. Eventually, networking and personal computers extended the accomplish of calculating activity. For quite a long time, though, most business-related computing tasks were performed within the office walls. Even as laptops became pop and people started working from a dwelling estimator, the piece of work was typically limited. Certain systems could not be accessed from habitation or certain tasks could not be completed because of low bandwidth. As engineering science has improved, many options are now available for enabling remote work. One of the most popular is remote desktop.
Remote Desktop Defined
Remote desktop services provide a user on one estimator access to another computer. The second computer may be in a completely split location, just the user has access and remote command just as if they were working on their local system.
The 2d computer could be in a different location, it could be a desktop or mobile device, or it could exist a virtual machine. In that location are many ways of enabling remote desktop, depending on the needs of the organization.
Remote desktop (or virtual desktop) solves two issues related to remote work:
- Remotely accessing files on a local network
- Eliminating bandwidth issues
Kickoff, if the finish user is accessing a corporate organisation, the IT team can make all corporate applications bachelor. All the work is still existence washed within the corporate network, and the data never has to leave the corporate confines, reducing cybersecurity vulnerabilities.
2nd, bandwidth issues are restricted to the user interface. Bandwidth is a measure of how much data travels across network connections. If an employee is working on an application at home and and so has to send all the information dorsum to corporate servers, that can become cumbersome.
With remote desktop, all the actual compute work is being washed at some other location, so there is no business concern over massive amounts of data having to travel back and forth. Low bandwidth can still create an unpleasant feel for the stop user, but the work itself is not impacted virtually equally much.
Pros and Cons of Remote Desktop
While the pros of using remote desktop include increased security and eliminating bandwidth issues, there are downsides every bit well.
The primary downside to remote desktop is that it becomes a separate application that the Information technology team has to maintain. Many companies are exploring cloud options as an alternative to remote desktop software, since that removes a layer of complexity.
This has get increasingly popular equally home networks have go more than robust, only remote desktop is even so used in many situations where applications cannot be migrated to the cloud or the company has not nonetheless pursued a strong cloud architecture.
Remote Desktop vs. VPN
Remote desktop and virtual private network (VPN) are both methods for connecting a remote employee to corporate systems, but they employ to unlike parts of the workflow.
Remote desktop gives a user access to a computer in a different location. This access tin be delivered over any kind of network connection.
VPN, on the other hand, refers to the connectedness itself. Rather than relying on the open internet, VPN creates a secure tunnel between the remote user and the corporate systems. This tunnel can and then exist used for remote desktop or for other types of applications that crave a secure connection.
How Does Remote Desktop Piece of work?
At that place are two main pieces that become into making a remote session functional. The first slice is the protocol that allows information to pass from i figurer to another. This defines data transmission and graphical components. There are open-source protocols – like remote framebuffer (RFB) – and proprietary protocols – like Remote Desktop Protocol (RDP) from Microsoft and Independent Computing Architecture (ICA) from Citrix.
However, most IT staff will non need to exist experts in protocols. Instead, the important piece for Information technology pros is the 2nd piece, the application that uses the protocols to create the connection. Every remote desktop application has one component installed on the cease-user machine and one installed on the reckoner or server that is acting every bit the host.
Here are examples of common applications used for each protocol:
- Virtual Network Computing (using RFB)
- Remote Desktop Connection (using RDP)
- XenApp (using ICA).
The choice of awarding volition depend on budget, required features and existing architecture. The standard applications that come bundled with operating systems, such equally Microsoft'southward Windows Remote Desktop Connection or Google's Chrome Remote Desktop, are more suited for individual apply. Enterprise applications, such equally RemotePC or Connectwise Control, have more than features for assistants and squad use.
How to Set up Remote Desktop in Windows x
For wide enterprise usage, there are two bones steps for setting upward remote desktop:
- Offset, the host calculator or server must be able to receive remote requests.
- 2nd, every endpoint must have a customer that tin can connect to the host.
The details for these steps will differ for every awarding, but the basic concept will exist the same.
Beyond any large-scale rollout of a remote desktop application, there may be cases where individual connections make sense. For example, a help desk technician may need access to a auto to check settings while debugging a problem.
The basic steps for an private connectedness are the same, but with near companies using Windows environments, there is an opportunity to leverage the built-in application from the operating system.
How to Fix a Host Computer to Receive Remote Requests
- Assuming the host PC is running Windows 10 Pro, the Remote Desktop application is plant under Showtime> Settings > System. Alternatively, the application tin exist found by clicking Start and typing "Remote Desktop Settings" in the search field.
- Once the application is open up, select "Enable Remote Desktop."
- The name of the PC will be needed to make the remote connection. To easily find the name of the PC, click the Start button and type "Figurer Name," then select "View your PC name" from the search results.
The host PC can at present be accessed from another remote computer, either a Windows machine, a Mac or a mobile device.
How to Connect to a Host Estimator from an Endpoint
Here's how to connect a host reckoner to another Windows motorcar, a Mac or a mobile device.
- Windows: On a Windows machine, click the commencement push and type "Remote Desktop Connection" in the search field. Once the Remote Desktop Connection application is open, enter the proper name of the host PC and click connect.
- Mac, iOS, or Android Device: Download the Microsoft Remote Desktop app from the appropriate app store. Once the app is installed, the connexion can be fabricated by entering the name of the host PC.
Note that these uncomplicated connections crave both computers to be on the same network. To enable access exterior the local area network, the Information technology team must either configure port forwarding on the router or provide a VPN connection. Port forwarding tin create security vulnerabilities, and so it would typically not be used in a business organization setting. VPNs are more common, although they add complication by creating some other application layer that must be used and supported.
Common Remote Desktop Security Concerns
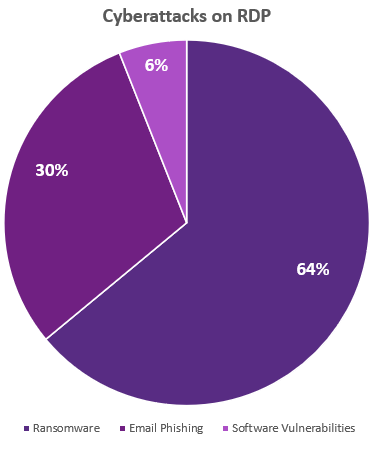
With the RDP protocol installed as a default option on Windows machines and used so widely considering of its convenience, it has become a prime number target for hackers. McAfee has plant that RDP accounts for 64% of the assault vectors for ransomware, compared to 30% for e-mail phishing and 6% from other software vulnerabilities.
One of the nearly straightforward ways to reduce the run a risk of RDP is to block all RDP connections exterior of the corporate network. Other enterprise applications tin can provide connectivity with greater security and a more robust feature set for IT administrators.
If in that location is an absolute need to allow RDP connections, there are other measures that tin amend security. First, consider authentication methods. As always, strong passwords should exist used. Hackers with enough calculating power can break fifty-fifty complex passwords but having proper passwords in place will ward off those hackers looking for a quick and easy target. Multifactor authentication is too a best practise.
2nd, network administrators can monitor for failed login attempts. As well many failed attempts from a unmarried user ID or IP accost can indicate a brute-forcefulness assail. Monitoring failed logon attempts or flagging failed attempts that cross a certain threshold are adept examples of activities that tin can be automated.
Remote access has become essential in the wake of COVID-19. Whether using default operating system methods or specific enterprise applications, IT pros can help increase workforce productivity and better employee flexibility.
IT support professionals, like help desk technicians, install, manage and troubleshoot remote desktop at their organizations. Go the skills needed to work in IT support with CompTIA A+. Download the exam objectives for complimentary to see what skills are covered.
Explore More Resources
gulbransonbittly59.blogspot.com
Source: https://www.comptia.org/content/articles/what-is-remote-desktop
0 Response to "Comptia Network+ Â⮠Lab Series Network Concepts Lab 7 Remote Access - Rdp 23 Review Questions"
Post a Comment